How Hackers Can Get Their Hands On Your Personal Information
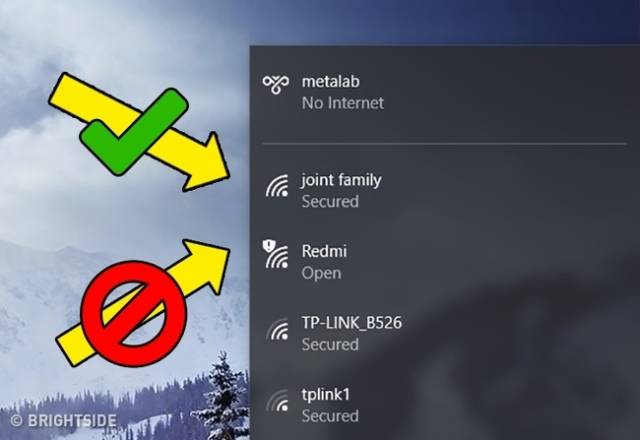
Unsecure Wi-Fi networks
Open Wi-Fi, or Wi-Fi that doesn’t require a password, is basically free access to all of your files. Every activity you do can be monitored by a hacker on the same Wi-Fi network.
If it becomes absolutely necessary to use Open Wi-Fi, like a public hotspot, use VPN (Virtual Private Network) to secure your Wi-Fi channel.
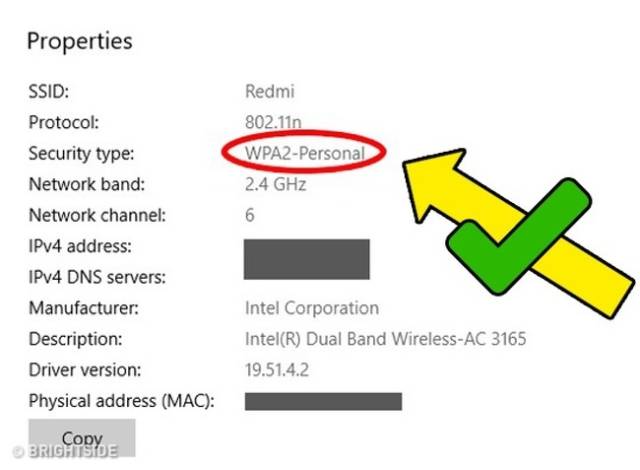
Weak encryption and lack of PIN for Wi-Fi router
Use only strong protocol WPA (Wi-Fi Protected Access) which is stronger than WEP (Wired Equivalent Privacy) and cannot be easily hacked by hacker.
This property will be changed on the router’s webpage. Also, hackers use WPS (Wi-Fi Protected Setup) vulnerability to hack Wi-Fi passwords even if you use WPA. So, it`s better to turn off the WPS method of authentication on your router’s web page.
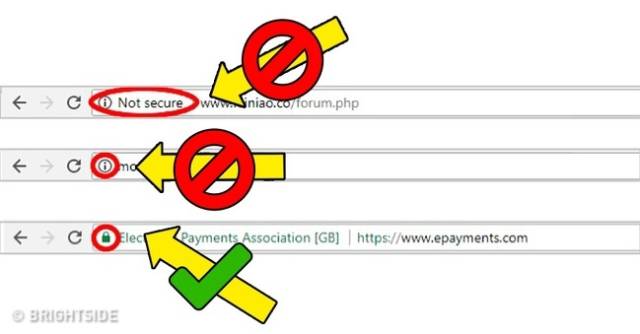
Unsecure sites
Sites without the lock symbol are really suspicious and can be used to get information from your computer without your authorization using a MIM (man-in-the-middle) attack.
Also, if you`re dealing with sites where login details are required like bank sites, check for the green bar alongside green lock.
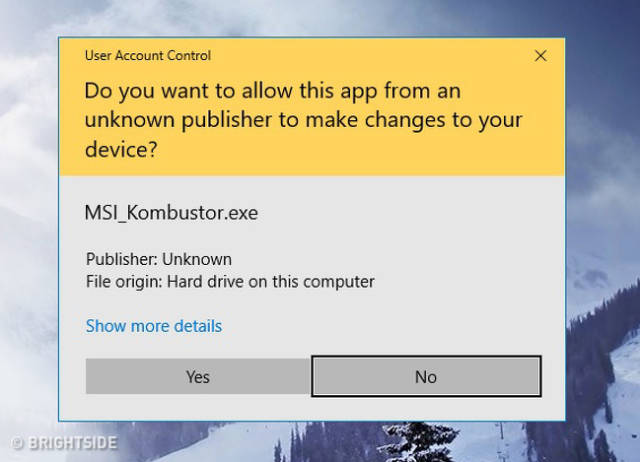
Unknown programs
Allowing programs that you`re unfamiliar with (malware) or whose names you haven’t heard of might seriously damage the security of your computer, and a hacker could easily extract your passwords.
If you’ve allowed something like this, you might want to delete that piece of software and run a thorough scan by your anti-virus software.
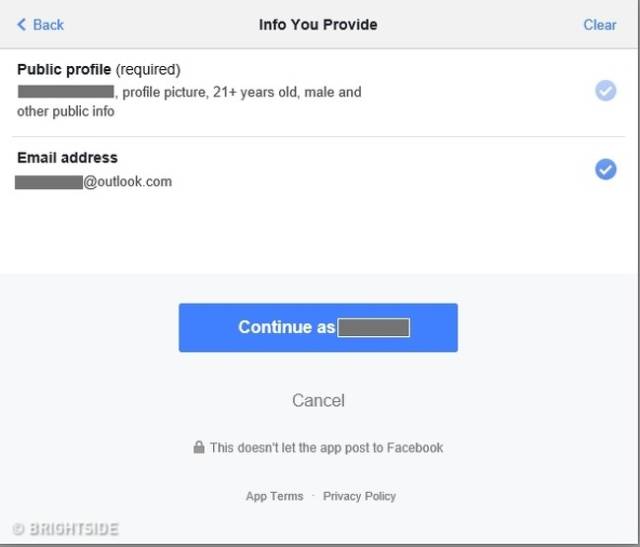
Your approval of account links to unknown sites
Linking Facebook or Twitter accounts to a suspicious site allows the site to gain your personal information which could be used against you.
Try not to link your account to whichever sites request it. Make sure you link it only when it’s an absolute necessity.
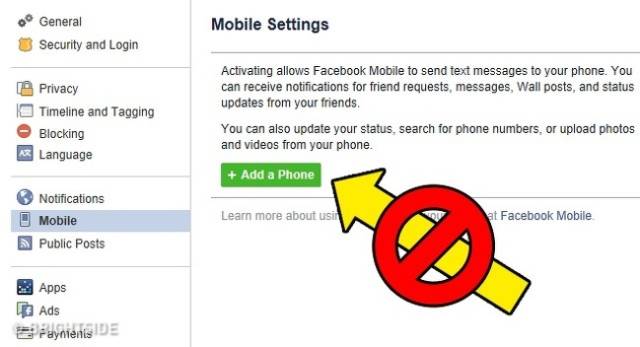
Revealing your mobile number for social media login
Hackers have found a flaw in Facebook and other social media networks to gain access to your account by using the “Forgot Your Password” function and diverting the messages from your mobile phone using a SS7 (Signalling system number 7) flaw in their system.
Don`t link your phone number with your social media networks. Instead use your username or email-address for login.
No Windows OS upgrade
Don`t use Windows XP, or an older version of Windows. They have a greater risk of getting hacked. The security updates for Windows XP and older versions have been terminated by Microsoft.

No Sandbox
If you want to be more secure while visiting scrupulous sites, simply use a software called “Sandbox.”
Sandboxing basically restricts the software in a protected environment allowing only the basic resources and restricting any additional permissions it needs access to, like for example, your computer files.
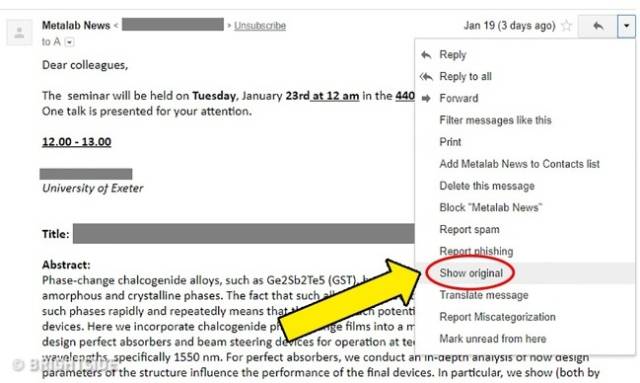
Suspicious email and attachments
Hackers use a SMTP (Simple Mail Transfer Protocol) header injection to insert malicious viruses, spam, and phishing websites onto a victim’s computer.
Don’t open mail that looks like spam and don’t open unknown attachments. Instead, first scan the file using anti-virus software and always check the header of the email.
Synchronized data
Hackers can attack cloud servers using various attacks, like a DDOS (Distributed Denial of Service) attack or a man-in-the-cloud attack, to access your data and passwords.
Always backup your data offline to an external storage device like a hard drive or a flash drive.
